The beauty of encryption
The pwcrypt tool can be used to obfuscate passwords in various config files. As you can see in the visible fragments in the picture below, it follows a nice pattern. It can be easily extracted with a standard spreadsheet tool once you understand the underlying principle. As you can see in the picture, it is even possible to extract control characters that you can not enter on the keyboard.
Is this a problem? Well, pwcrypt only protects data that should already be protected anyway. Obscurity is a valid security layer when used as part of a comprehensive security strategy. But obscurity mainly improves perceived safety, it never should be your first choice.
The purpose of this article is therefore very simple: It is an invitation to question yourself. Who has access to your IT environment? How are things maintained? How often to you question your routine?
If you do not know where to start, here is some inspiration:
https://ist.mit.edu/security/tips
https://ist.mit.edu/security/protecting_data
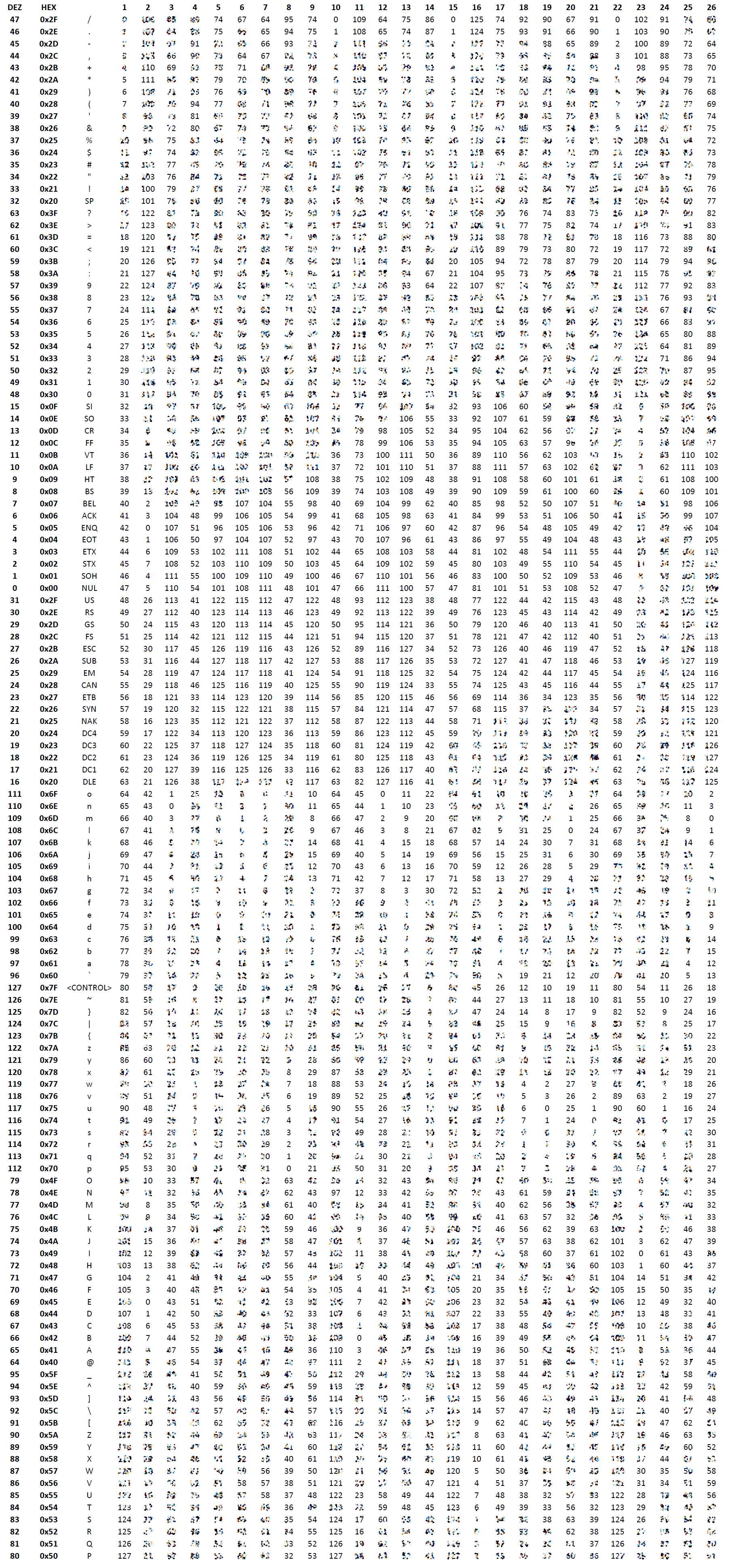
For information purposes only. Use at your own risk!