Building a (PLM) fortress
 Integrating your PLM software into other systems in your organization is a common standard. Usually you connect your CAD systems or your ERP. At a certain point, of course, you also want to connect your software to your suppliers or external partners. Most available PLM systems provide you with the appropriate security features to accomplish this task. But do they really cover everything? Let’s find out!
Integrating your PLM software into other systems in your organization is a common standard. Usually you connect your CAD systems or your ERP. At a certain point, of course, you also want to connect your software to your suppliers or external partners. Most available PLM systems provide you with the appropriate security features to accomplish this task. But do they really cover everything? Let’s find out!
Before I get to the topic, I would like to start this article with a small anecdote: My first encounter with Aras was 2015 in Munich. I attended a training class to learn the basics of their software. I can highly recommend the training, although the actual learning phase starts afterwards (and somehow never ends). During the training I discovered a small typo in Innovator (IR-037929). Nothing really worth mentioning, but of course I proudly showed my discovery to the trainer:
Me: “Hey I found a bug! There’s a typo!”
Trainer: “Wow, I never have seen this one before.”
Me: “Do I get something when I report it?”
Trainer: “Well, you probably have to find more than one typo.”
Me: “How much more?”
Trainer: “Oh, save your time. We have a lot of big customers and IT experts who work with the software. I do not think y o u will ever find more than one typo…”
The way he pronounced that sentence again showed me the misery of my existence: To be a redneck version of Computer Engineer Barbie in the conservative world of PLM. Of course I accepted the challenge! Four years later I now have my own PLM blog where I can share all my wonderful discoveries and ideas with the world.
But what should I write, which is not already written on other blogs? PLM is much more than just using a piece of software provided by one of the various vendors. It is about managing one of the most valuable resources in your company: Data! In particular, administrators and technicians must have a strong attitude that reflects the importance of this task. This attitude must be reflected in our actions. I am sure everybody would a agree to this inspirational statement.
And yet I have seen far too many companies that love to talk about the importance of secure data handling, while already their websites represents the exact opposite. But who will be the first to cast a stone? We all have to ask ourselves if we really live up to what we preach.
What to learn from WordPress
I use WordPress to manage this blog. A proven content management system that includes everything you need to build a beautiful website or blog.
Really everything? Technically yes! But I soon realized that not everything is included out of the box:
- How do I ensure system stability and speed?
- What about backups?
- How do I fulfill legal requirements, especially GDPR?
- How do I deal with all the bots that are constantly attacking my blog as early as 24 hours after I first hosted the website?
- How do I prevent abusive behavior from site visitors who know WordPress better than me?
Ensuring the general functional safety of the blog sounded reasonable. But GDPR and all the other laws? So much work that nobody will ever honor or even notice. One solution suddenly seemed very obvious to me. Why do not I just ignore it? Like many other websites too? No court in the world cares about non-commercial hobby blogs.
But is that really the attitude that a PLM blog should have? How can my content be credible if the website itself is a negative example? The result: At the time of this article, I spent more time on legal topics than on actual blog content!
Nevertheless, I do not regret the effort. Because after many hours of work, I suddenly had a moment of enlightenment: PLM systems are just like WordPress! Every PLM software on the market offers a wide range of features. But just like WordPress, you will also need to adapt your PLM. And that’s totally ok. Because every blog is different, just like every company.
In the same way, all common PLM systems will provide you the necessary level of security you need for your daily business tasks. But just like WordPress, no PLM system can provide OOTB solutions for all of the various tasks that may arise while using the software.
Once you plan to open your PLM for your supply chain, you may have questions similar to mine:
- How do we secure the data in our PLM so that people can only see what they are supposed to see?
- What about GDPR?
- Does the EU Cookie Law affect us?
- What about terms and conditions?
- How do we protect our website from attackers?
- …
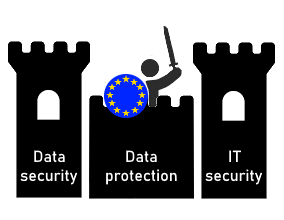
Data security vs. data protection
In the context of PLM, we can break down the topic into three areas:
- Data protection
This one deals with the protection of personal data. Within our PLM system these are typically general personal data (name, address, e-mail address,..) or online data (IP address, location data,..) - Data security
In contrast to data protection, data security deals with the protection of data, regardless of whether they are related to a person. Within your PLM system, this term refers to the protection of confidential data, such as CAD drawings. - IT security
Refers to the protection of the technical processing of information. This includes above all the error-free function and the reliability of the IT systems.
Most PLM systems will already provide you an adequate level of data security. But just like WordPress, no PLM vendor can offer you an out-of-the-box complete solution for data protection and IT security.
In a couple of upcoming articles we will take a closer look at these three blocks. Stay curious!